Short overview between classical computing and quantum computing.
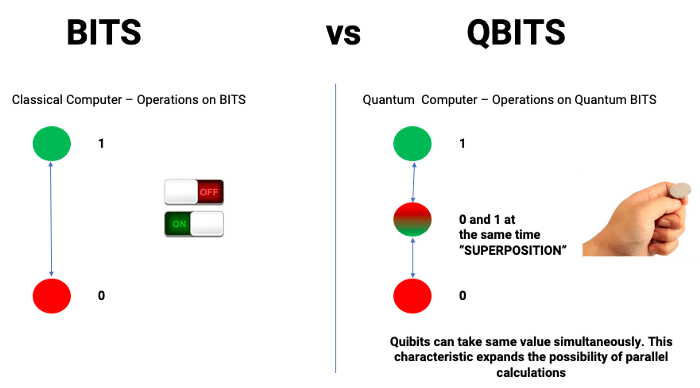
Classical computers carry out logical operations using the definite position of a physical state. These are usually binary, meaning its operations are based on one of two positions. A single state – such as on or off, up or down, 1 or 0 – is called a bit.
Quantum computers perform calculations based on the probability of an object’s state before it is measured – instead of just 1s or 0s.
This means that quantum computers have the potential to process exponentially more data compared to classical computers.
Quantum computers on cybersecurity.
In cybersecurity, quantum computers are depicted as the breakers of the current encryption running our world, making our data private, guarding it against prying eyes. Should we be afraid? The short answer is no, although the potential for quantum computers to break RSA 2048 (one of today’s most powerful and secure encryption forms) in as little as 8 hours is possible, for it to happen quantum computing technology would have to advance much more.
As it stands right now our state-of-the-art quantum computers can use 70 qubits, to reach the 8-hour cracking time researchers estimate that a 20 million-qubit quantum computer would be required.
NIST predicts that quantum computing regarding the cracking of RSA will take 15 years, while some researchers predict as little as 5 years.
So, should we be worried about the next 5 or 15 years? Thankfully the answer is also no, quantum technology is not exactly new, and a lot of theory is already available, as such security researchers have already developed what are called post-quantum codes that even a quantum computer would not be able to crack. So, it is already possible to safeguard data today against future attacks by quantum computers. But these encryption methods are not yet used as standard.

What about data previosly captured on traffic?.
In 5 or 15 years, whenever or if advanced quantum technology would be plentifully available to the public, there is a risk that data captured by a malicious actor, could then in the future be decrypted. For the average person, this is not worrisome, for example, data decrypted regarding credit card data would be worthless in the future, however for governments and entities that rely on secrecy this could arise to be a very big issue, as disclosure of classified data even if 5, 15 years old could be very impactful.
Conclusion.
Although quantum computing is relatively far away in order to disturb our present ecosystem in the digital world, measures and standards should be implemented in a timely manner(post-quantum codes) in order to safeguard future data.
By Andre Gomes



